
Okay, let's be honest, nobody really wants to spend their day reading about cybersecurity. It's kind of like flossing – you know you should do it, but it's not exactly the most thrilling activity. But here's the thing: in today's world, cybersecurity is just as important as flossing, maybe even more so. Why? Because just like neglecting your dental hygiene can lead to painful toothaches and expensive dental bills, neglecting cybersecurity can lead to devastating data breaches, financial losses, and a whole lot of headaches.
So, what exactly is cybersecurity? In a nutshell, it's the art of protecting your computer systems, networks, and data from those digital delinquents who want to steal your information, disrupt your operations, and generally cause mayhem. Think of it as your digital guardian angel, keeping your business safe from the lurking dangers of the cyber world.
Now, I know what you're thinking: "Cybersecurity sounds complicated and boring." But trust me, it doesn't have to be. This pillar page is your one-stop shop for all things cybersecurity, breaking down the complex concepts into bite-sized pieces and serving them up with a side of humor. We'll explore the importance of cybersecurity, the common threats you need to watch out for, the best practices to keep you safe, and the emerging trends that are shaping the future of cybersecurity.
By the time you finish reading this page, you'll be a cybersecurity whiz kid, ready to take on the cyber world with confidence. You'll understand why cybersecurity is so crucial for your business, how to protect your valuable data, and what steps you can take to stay ahead of those pesky cyber villains. So, grab a cup of coffee, settle in, and let's embark on this cybersecurity adventure together.
The Importance of Cybersecurity: Why It Matters
Okay, so we've established that cybersecurity is kind of a big deal. But why exactly? Is it really worth all the fuss? In a word, yes.
Think of your business as a house. You've got valuable stuff inside – customer data, financial records, trade secrets – all the things that keep your business humming. Now, imagine leaving your front door wide open, no locks, no security system, nothing. That's basically what it's like to operate without proper cybersecurity. You're practically inviting cybercriminals to waltz in and help themselves to your precious assets.
A cyberattack can be a real nightmare for any business. It can lead to:
- Financial Losses: Dealing with a data breach can cost a pretty penny. You've got legal fees, regulatory fines, customer notification costs, not to mention the potential loss of revenue from disrupted operations. Ouch!
- Reputational Damage: In today's world, news travels fast. A single cybersecurity incident can tarnish your company's reputation faster than you can say "data breach." And once that trust is broken, it can be tough to win back your customers' confidence.
- Legal Liabilities: Depending on your industry and where you operate, you might be subject to strict data protection regulations. Failing to comply with these regulations can land you in hot water with the authorities, leading to hefty fines and legal battles.

But cybersecurity isn't just about avoiding these negative consequences. It's also about creating a strong foundation for your business to thrive in the digital age. Here's how:
- Protecting Sensitive Data: Whether it's customer information, financial records, or intellectual property, your data is the lifeblood of your business. Cybersecurity helps you safeguard this valuable asset, ensuring its confidentiality, integrity, and availability.
- Ensuring Business Continuity: Nobody wants to deal with downtime. Cybersecurity helps you keep your systems running smoothly, even in the face of cyberattacks or other disruptions. It's like having a backup generator for your business, ensuring that you can continue operating even when the lights go out.
- Maintaining Customer Trust: In today's digital world, trust is everything. Customers want to know that their data is safe in your hands. A strong cybersecurity posture demonstrates your commitment to protecting their information, building trust and loyalty that can translate into long-term success.
So, there you have it. Cybersecurity is not just a technical necessity; it's a strategic imperative for any business that wants to succeed in the digital age. It's about protecting your assets, maintaining your operations, and building trust with your customers. In other words, it's about securing your future.
Key Cybersecurity Concepts: The Building Blocks
Alright, now that we know why cybersecurity is important, let's get into the what. Just like any superhero has their unique gadgets and gizmos, cybersecurity has its own set of tools and tricks. But before we get to those, we need to understand the basic building blocks.
Think of these concepts as the foundation of your cybersecurity fortress:
- Confidentiality: This is all about keeping your secrets... well, your data secrets. It's like having a vault where only authorized personnel can access sensitive information. Think of it as the "need-to-know" principle in action, ensuring that only those who absolutely need access to sensitive data can get their hands on it. We're talking passwords, encryption, access controls – the whole shebang.
- Integrity: Picture this: you're about to bake a batch of cookies (because who doesn't love cookies?), and you realize someone swapped the sugar for salt. Disaster! Data integrity is kind of like that. It's about making sure your data is the real deal – accurate, complete, and untampered with. Because in the digital world, data integrity is paramount, ensuring that the information you rely on is accurate and trustworthy.
- Availability: Imagine trying to watch your favorite show, but the streaming service keeps crashing. Frustrating, right? That's what lack of availability feels like. In the cybersecurity world, availability means making sure your systems and data are ready to go when you need them. It's like having a reliable car that always starts, so you can get where you need to go without any hiccups.
- Risk Management: Life is full of risks, and the cyber world is no exception. Risk management is about identifying potential threats and figuring out how to deal with them. It's like scouting out the cyber landscape for potential dangers and coming up with a plan to stay safe. Because in the world of cybersecurity, it's not a matter of "if" but "when" an attack will occur, and being prepared is half the battle.
- Vulnerability Management: Even the strongest fortress has its weak points. Vulnerability management is about finding and fixing those weak spots before the bad guys can exploit them. It's like patching up holes in your fence to keep unwanted visitors out. Because in the cyber world, vulnerabilities are like open doors, inviting attackers to stroll in and wreak havoc.
- Incident Response: Okay, let's be real, even with the best defenses, sometimes things go wrong. Incident response is about having a plan to deal with cyberattacks and recover quickly. It's like having a fire drill for your computer systems – everyone knows what to do in case of an emergency. Because when a cyberattack hits, every second counts, and a well-rehearsed incident response plan can minimize the damage and get you back on your feet faster.
These concepts might seem a bit abstract, but they're the bedrock of any solid cybersecurity strategy. Understanding them is like having a secret decoder ring for the cyber world, helping you make sense of the threats and defenses that keep your business safe.
Common Cybersecurity Threats: Know Your Enemy
Okay, now it's time to meet the bad guys. The cyber world is like a digital Wild West, full of outlaws and bandits looking to cause trouble. These cybercriminals are constantly coming up with new and creative ways to infiltrate your systems, steal your data, and disrupt your operations.
First up, we have malware, the sneaky saboteur of the digital world. Malware is like a digital virus, infecting your computers and wreaking havoc on your systems. It comes in all shapes and sizes, from viruses and worms to ransomware and spyware. These malicious programs can steal your data, corrupt your files, or even lock you out of your own systems until you pay a ransom. Think of it as the digital equivalent of a nasty cold – it can slow you down, cause a lot of discomfort, and even lead to more serious complications if left untreated.
Next, we have phishing, the master of disguise in the cyber world. Phishing attacks are like wolves in sheep's clothing, using deceptive emails and websites to trick you into giving up your sensitive information. They might pose as your bank, your boss, or even a long-lost relative, all in an attempt to get you to click on a malicious link or download a malware-laden attachment. So, be wary of those too-good-to-be-true offers and unexpected emails, and always double-check the sender's address before clicking on anything.
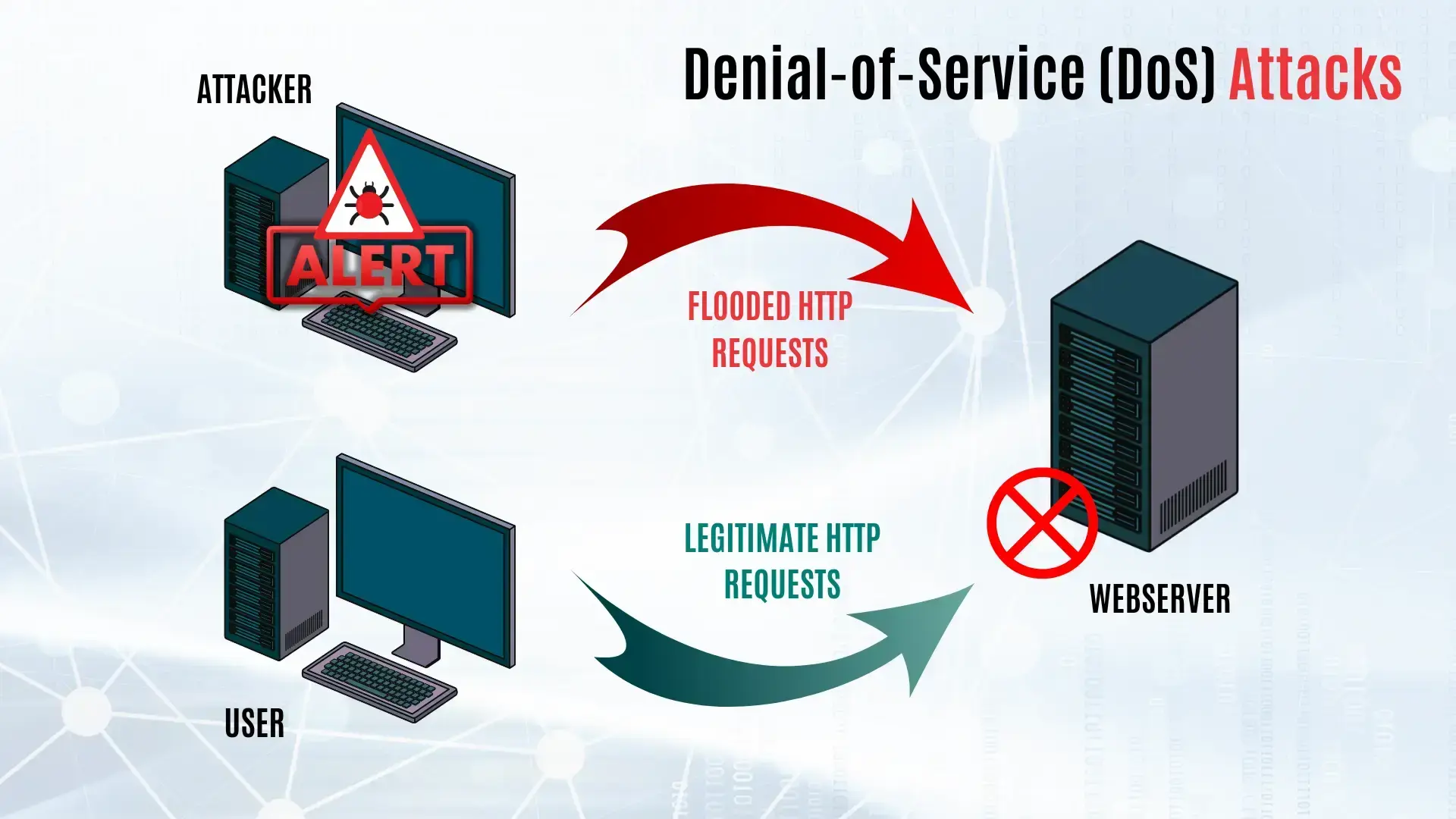
Then there are denial-of-service (DoS) attacks, the digital equivalent of a traffic jam. These attacks flood your systems with so much traffic that they become overwhelmed and unavailable to legitimate users. It's like someone blocking the entrance to your store, preventing customers from getting in and doing business with you. DoS attacks can disrupt your operations, damage your reputation, and even cost you money in lost revenue.
SQL injection is a more technical attack that targets your databases. It's like a hacker sneaking in through a backdoor to mess with your data. SQL injection attacks exploit vulnerabilities in web applications to inject malicious code into your databases, allowing attackers to steal sensitive information, modify your data, or even take control of your entire system.
And finally, we have man-in-the-middle (MitM) attacks, the eavesdroppers of the cyber world. These attacks intercept communication between two parties, allowing attackers to steal data, spy on your conversations, or even manipulate the information being exchanged. It's like someone listening in on your phone calls or reading your emails without your knowledge. MitM attacks can be particularly dangerous because they can go undetected for long periods, allowing attackers to gather sensitive information and cause significant damage before you even realize what's happening.
So, there you have it – a rogue's gallery of common cybersecurity threats. By understanding these threats and how they work, you can take steps to protect your business and stay one step ahead of the bad guys. Remember, in the cyber world, knowledge is power. The more you know about your enemies, the better equipped you'll be to defend yourself.
Cybersecurity Best Practices: Your Defensive Arsenal
Alright, enough with the doom and gloom! Now that we've met the villains, it's time to suit up with our cybersecurity armor. Think of these best practices as your secret weapons in the fight against cybercrime.
Strong Passwords: The First Line of Defense
Let's be honest, we've all been guilty of using weak passwords at some point. "Password123" or our pet's name might be easy to remember, but they're also easy for hackers to crack. Your passwords are like the gatekeepers to your digital kingdom, so make sure they're strong, unique, and complex. Think of it as creating a secret handshake that only you and your account know. And if you're struggling to remember all those complex passwords (who isn't?), a password manager can be your trusty sidekick.
Multi-Factor Authentication (MFA): Double the Trouble for Hackers
Imagine having a second lock on your front door. Even if someone manages to pick the first lock, they're still stuck. That's the idea behind multi-factor authentication (MFA). It adds an extra layer of security by requiring you to provide multiple forms of identification before you can access your account. It's like having a secret code that changes every time you log in. So, even if someone steals your password, they'll still need that second factor (like a code sent to your phone) to get in.
Software Updates: Keeping Your Systems Healthy
Those pesky software update notifications might seem annoying, but they're actually your friends. Think of them as booster shots for your computer, protecting it from the latest digital diseases. Software updates often include security patches that fix vulnerabilities and keep your systems healthy and strong. So, next time you see that update notification, don't ignore it. Just click that "update" button and give your computer the protection it deserves.
Firewall Protection: The Gatekeeper of Your Network
A firewall is like a security guard for your network, standing watch and keeping those unwanted visitors out. It's like having a moat around your castle, protecting it from invaders. Firewalls act as a barrier between your internal network and the outside world, blocking unauthorized access and keeping your data safe from harm.
Intrusion Detection and Prevention Systems (IDPS): The Cyber Detectives
If firewalls are the security guards, then intrusion detection and prevention systems (IDPS) are the cyber detectives. These systems are constantly monitoring your network for suspicious activity, like those sneaky hackers trying to break in. Think of them as your digital bloodhounds, sniffing out those cyber threats and stopping them in their tracks.
Data Encryption: Making Your Data Unreadable to the Bad Guys
Encryption is like writing your secrets in a code that only you can decipher. It scrambles your data, making it unreadable to anyone who doesn't have the key. This is especially important for sensitive data like customer information and financial records. So, encrypt your data, both in transit and at rest, and keep those cyber thieves guessing.
Regular Backups: Your Safety Net
Imagine losing all your important files – photos, documents, everything. It would be a disaster, right? That's why regular backups are so important. They're like your safety net, ensuring that you can recover your data even if your system crashes or gets attacked by ransomware. Think of it as having a spare tire in your car – you might not need it every day, but you'll be glad you have it when you do.

Employee Security Awareness Training: Empowering Your Human Firewall
Your employees are the first line of defense against cyberattacks. But even the most well-meaning employee can fall victim to a phishing scam or accidentally click on a malicious link. That's where security awareness training comes in. It's like giving your employees a crash course in cybersecurity self-defense, teaching them how to spot threats, avoid common pitfalls, and protect themselves and the company from harm.
By implementing these best practices, you can build a robust cybersecurity posture and keep your business safe from those pesky cyber villains. Remember, cybersecurity is not a one-time event; it's an ongoing process. So, stay vigilant, stay informed, and stay ahead of the game.
Emerging Cybersecurity Trends: Staying Ahead of the Curve
Hold on tight, because the cybersecurity landscape is evolving faster than a teenager's music taste! What worked yesterday might be obsolete tomorrow, so staying ahead of the curve is critical. Think of it like trying to hit a moving target – you need to anticipate where it's going, not just where it is now. One of the biggest game-changers is the rise of artificial intelligence (AI) and machine learning (ML). These technologies are like the superheroes of cybersecurity, using their super-smarts to analyze massive amounts of data, detect suspicious patterns, and predict attacks before they even happen. It's like having a crystal ball that can see into the future of cyber threats, giving you a heads up on what to watch out for.
But that's not all. The way we store and access data is changing too, with cloud computing becoming the go-to solution for businesses of all sizes. It's convenient, it's scalable, and it's got everyone migrating their data to the digital cloud. But this also means we need to rethink our security strategies. Protecting your data in the cloud is like building a fortress in the sky – you need strong defenses, vigilant guards, and a whole arsenal of cloud-specific security measures to keep those cyber villains at bay. And let's not forget about the Internet of Things (IoT) – that ever-growing network of connected devices, from smart refrigerators to industrial sensors. While these gadgets are cool and convenient, they also create new entry points for cyber attackers. It's like having a house with a million windows – you need to make sure each one is locked and secured to keep those cyber burglars out. And then there's blockchain technology, the new kid on the block with the potential to revolutionize cybersecurity. It's like a digital ledger that's impossible to tamper with, creating an unbreakable chain of trust for securing data and transactions. So, buckle up and get ready for a wild ride, because the future of cybersecurity is full of exciting possibilities and challenges. By staying informed and embracing these emerging trends, you can ensure your business is prepared for whatever the cyber world throws your way.
Cybersecurity Frameworks and Standards: The Rules of the Road
Alright, let's talk about the rulebook for staying safe in the cyber Wild West. Just like any civilized society needs laws and regulations to keep things in order, the cyber world has its own set of frameworks and standards to guide businesses on their cybersecurity journey. Think of these frameworks as your trusty map and compass, helping you navigate the complex terrain of cybersecurity and stay on the right path.
NIST Cybersecurity Framework: Your Cybersecurity GPS
The NIST Cybersecurity Framework is like your cybersecurity GPS, providing a roadmap for managing and reducing cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), this framework is a voluntary set of standards, guidelines, and best practices that helps organizations of all sizes improve their cybersecurity posture. It's like having a trusted guide by your side, helping you identify your cybersecurity needs, prioritize your efforts, and measure your progress.
ISO 27001: The Gold Standard for Information Security
ISO 27001 is like the gold standard for information security management. It's an internationally recognized standard that provides a framework for establishing, implementing, maintaining, and continually improving an information1 security management system2 (ISMS). Think of it as a seal of approval, demonstrating to your customers, partners, and stakeholders that you take information security seriously and have implemented a robust security management system.
CIS Controls: Your Cybersecurity Checklist
The CIS Controls are like your cybersecurity checklist, providing a prioritized set of actions for cyber defense that provide specific and actionable ways to stop today's most pervasive and dangerous attacks.3 Developed by the Center for Internet Security (CIS), these controls offer a clear and concise roadmap for improving your cybersecurity defenses. They're like a recipe for cybersecurity success, guiding you through the essential steps to protect your systems and data.
These frameworks and standards might seem a bit daunting at first, but they're invaluable resources for any business that wants to build a strong cybersecurity foundation. They provide a structured approach to cybersecurity, helping you identify your risks, implement effective controls, and measure your progress. So, don't be afraid to embrace these frameworks and use them as your guide on your cybersecurity journey. After all, in the cyber world, it's always better to be safe than sorry.
Cybersecurity and Monreal IT: Your Trusted Partner in the Digital Age
Okay, let's shift gears for a moment and talk about how Monreal IT can help you navigate the wild and woolly world of cybersecurity. We're not just another IT company; we're your trusted partner in the digital age, committed to helping you protect your business and achieve your goals.
- Cybersecurity is in our DNA: At Monreal IT, cybersecurity isn't just a service we offer; it's ingrained in everything we do. We live and breathe cybersecurity, constantly staying ahead of the curve to ensure your business is protected from the latest threats. Think of us as your cybersecurity superheroes, always on call to defend your data and systems from those pesky cyber villains.
- Delivering Desired Business Outcomes: We're not just about fixing computers and installing software; we're about helping you achieve your business objectives through the strategic use of technology. We work closely with you to understand your needs and challenges, developing customized solutions that align with your goals and help you maximize your technology investments.
- Consistently Earning the Title of Trusted Technology Experts: We're not just techies; we're trusted advisors. We take the time to understand your business, your industry, and your unique challenges, providing expert guidance and support to help you make informed decisions about your technology needs.
Our Cybersecurity Services: Tailored to Your Needs
We offer a comprehensive suite of cybersecurity services designed to meet the unique needs of your business. Whether you're a small startup or a large enterprise, we have the expertise and experience to help you build a robust security posture and protect your valuable assets.
- Managed Security Services Provider (MSSP) solutions: Our MSSP+™ solutions are like having a dedicated cybersecurity team on call 24/7. We monitor your systems, detect threats, and respond to incidents, so you can focus on what you do best – running your business.
- Vulnerability assessments and penetration testing: We're like the ethical hackers who try to break into your systems to find weaknesses before the bad guys do. This helps you identify and fix vulnerabilities before they can be exploited.
- Security awareness training: We help your employees become cyber-savvy with customized training programs. It's like giving your team a crash course in cybersecurity self-defense, so they can spot threats and avoid common pitfalls.
- Compliance and risk management: We're your partners in navigating the world of cybersecurity regulations and standards. We help you comply with the rules and develop a risk management framework that protects your business from potential threats.
Our Commitment to Excellence: CATIQ Values
At Monreal IT, we're guided by our core values of Commitment, Accountability, Teamwork, Integrity, and Quality (CATIQ). These values are at the heart of everything we do, ensuring that we deliver exceptional service and build lasting relationships with our clients.
Building Powerful Partnerships: Your Success is Our Success
We believe in building powerful partnerships with our clients and working together to achieve their business goals. Your success is our success, and we're dedicated to providing you with the support and expertise you need to thrive in the digital age.
So, if you're looking for a trusted partner to help you navigate the complex world of cybersecurity, look no further than Monreal IT. We're here to help you protect your business, achieve your goals, and thrive in the digital age.
Conclusion: The Cybersecurity Journey
Well, folks, we've reached the end of our cybersecurity adventure. Hopefully, you've learned a thing or two about the importance of protecting your business in this wild and wacky digital world. Remember that cybersecurity isn't just a one-time thing; it's an ongoing journey. It's like staying in shape – you need to keep exercising those cybersecurity muscles to stay strong and healthy.
So, what are you waiting for? It's time to take charge of your cybersecurity destiny! Embrace those best practices, stay informed about emerging trends, and don't be afraid to ask for help when you need it. After all, in the cyber world, it's always better to be safe than sorry.
And if you're looking for a trusted partner to guide you on your cybersecurity journey, look no further than Monreal IT. We're your local cybersecurity experts, committed to helping you protect your business and achieve your goals. So, give us a call, shoot us an email, or stop by our office for a chat. We're always happy to help you navigate the exciting and ever-changing world of cybersecurity.
Now go forth and conquer the cyber world! And remember, stay vigilant, stay informed, and stay safe.